Quick Answers
If you’re in a heated fluster trying to find a quick answer, please see them below. If you think one may apply in your scenario, please read the rest of the article.
You need to disable NetBIOS on each machine individually.
The NBNS (NBT-NS) traffic is part of a poisoner detection mechanism of your IDR.
Getting into it
Nothing is more frustrating than receiving a penetration retest report stating that a security vulnerability was not remediated at the time of retesting. Money, time, and reputation are all seemingly wasted when remediation attempts come up short. This is why it is especially important to ensure your security vulnerabilities, such as NetBIOS Name Service (NBNS) are fixed before retesting.
Disabling NetBIOS is a straightforward task. The default setting of Windows hosts is to follow the NetBIOS setting defined by the DHCP server. Disabling NetBIOS from the DHCP server, in most cases, will resolve the issue. However, this is not foolproof and may not resolve the issue on all hosts. Strafe Cybersecurity recommends directly disabling NetBIOS on each host if possible. The service can be disabled on each machine via PowerShell or the GUI on the WINS tab in Advanced TCP/IP Settings.
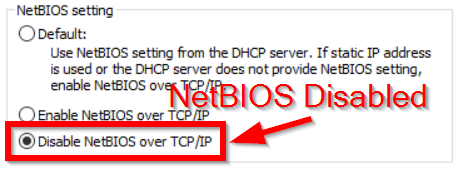
Could IDR be Responsible?
Understand Your Tools
With so many powerful security tools, it can be easy to lose track of all the incredible features that protect your network. Some of these protections may look like vulnerabilities but are deceiving attackers. This can be in the form of poisoner detection like we discussed in this post, or they can manifest in a different form such as honeypots or honeynets. No matter the manifestation, it is always good to have a full understanding of the tools you use to secure your network. Especially before a penetration test or retest where a lack of knowledge may result in a potentially costly false positive on a report.
LET'S HAVE A TALK
Just send us a quick message explaining your situation and get our price quote shortly. We can start by testing one part of your organization and expand as we move forward.
Or we can make an extensive testing & training plan and give you an unbeatable offer!
